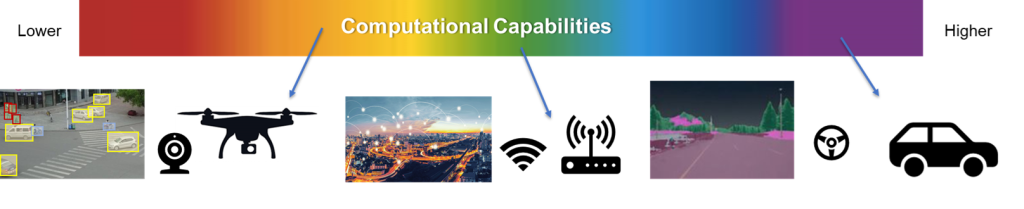
GuardAI’s Use Cases (UC) focus on high-risk application use-cases of edge AI Systems that take decisions and inform/take actions used in
- Critical infrastructures (e.g., transport), that could put the life and health of citizens at risk
- Essential private and public services
Test, and validate the novel tools to be developed in three edge AI Use Cases of broad interest, concerning diverse high-risk domain:
- Remote monitoring with drones (UC1)
- 5G network edge infrastructure (UC2)
- Autonomous vehicles (UC3)
The developed algorithms will be optimized and applied to each Use Case, taking into consideration their appropriateness and relevance, to provide increased capabilities.
UC1 – Robust Surveillance and Monitoring with AI-Enabled Drones
Summary:
AI-enabled drones equipped with RGB cameras, LiDAR, GPS, for the surveillance and monitoring of public spaces, such as city centres, transportation hubs, and critical infrastructure.
Scenarios/attack surfaces:
a) Tangible physical adversarial artifacts, such as affixing adhesive labels
b) Digital adversarial attacks aiming to manipulate the image pixel values and adding perturbations
Innovation:
a) Generative and unsupervised defence mechanisms with data from AIR,
b) Multi-sensor fusion from CEE for increased context-aware resiliency
c) Multi-agent module of CEE to gather predictions from multiple drones

UC2 – Protecting decentralized 5G network analytics
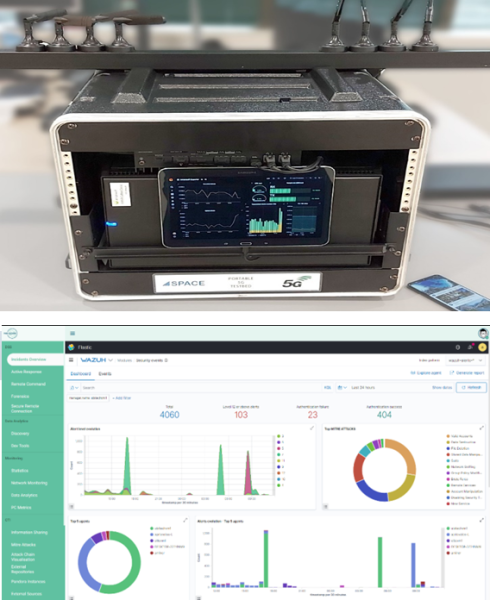
Summary:
Adversarial attacks on AI-enabled decentralized (edge-based) 5G Network Data Analytics Functions (NWDAF) running predictive analytics; anomaly detection; QoS optimization; load balancing and resource planning.
Scenarios/attack surfaces:
a) Adversarial attacks on 5G infrastructure (evasion/exploratory attacks, model inversion, trojan, GAN-generated waveform jamming, etc).
b) AI-based automated vulnerability assessment and ML-powered penetration testing
c) AI-assisted reinforcement learning-based anomaly detection
d) Stationary and mobile 5G testbeds will be employed
Innovation:
a) RL (deep Q learning), GANs and Transformers to generate adversarial attacks
b) RL models for attack detection
c) AI models for data denoising
UC3 – Resilient Perception in Connected Autonomous Vehicles
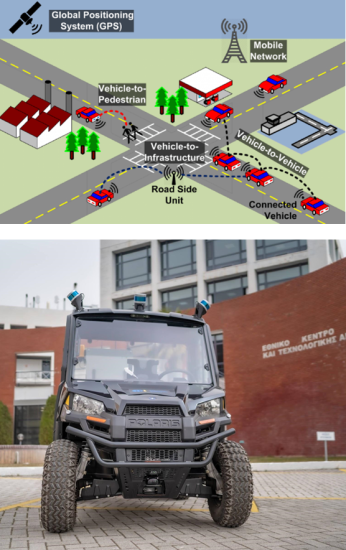
Summary:
Multi-modal and multi-agent co-operative awareness, to eliminate individual sensor deficiencies (adverse conditions, poor lighting occlusions, etc.), and protect system against cyber-attacks.
Scenarios/attack surfaces:
a) Test the co-operative situational awareness modelling based on real sensory inputs
b) Enhance safety indexes for autonomous driving by utilizing decentralized FL
c) 4D awareness for improved security in real and simulated digital twin environments
d) Adversarial attacks to the perception ML models (e.g., LiDAR jamming)
Innovation:
a) Multi-agent and multi-modal capabilities of CEE
b) Swarm Learning (SL) as a decentralized FL framework
c) Homomorphic encryption, ensuring data sovereignty, security, and confidentiality
d) Deep unrolling for increased robustness of perception algorithms.
